March 1, 2023
In an increasingly remote world with greater technological capabilities and solutions, information security is more important than ever. We’re seeing a significant increase in security breaches as attackers are getting smarter and more sophisticated.
In 2019, Microsoft reported a 95% increase in average cost per breach. As a result, victims ended up paying $5.16 million on average in damages. Much of the damage in these scenarios stems from ineffective response times. Microsoft states that 68% of breaches take months or even longer to discover.
It is not enough to be reactive – it is better to be proactive to stay ahead of attackers. Companies also need visibility into their security and compliance posture. If your industry follows some sort of regulatory standard, you want to be sure that you’re compliant across your information systems. If there are audit reports, you must ensure you have the required controls and audit trails in advance.
In order to achieve a proactive approach to security, the right tools for monitoring and remediation are necessary. One excellent option is Azure Security Center, which offers not only Azure-native security features but also works across hybrid environments.
Azure Security Center assesses the security state of your cloud resources. It works with IaaS (virtual machines, virtual network, network security groups), as well as with PaaS (app services, storage account, etc.) Workloads monitored by Security Center can be running in Azure, on-prem, and even in other cloud provider platforms, making it a true hybrid and multi-cloud security option.
Out of the box, Azure Security Center offers a base level of security posture management. This includes proactive security recommendations and a Secure Score.
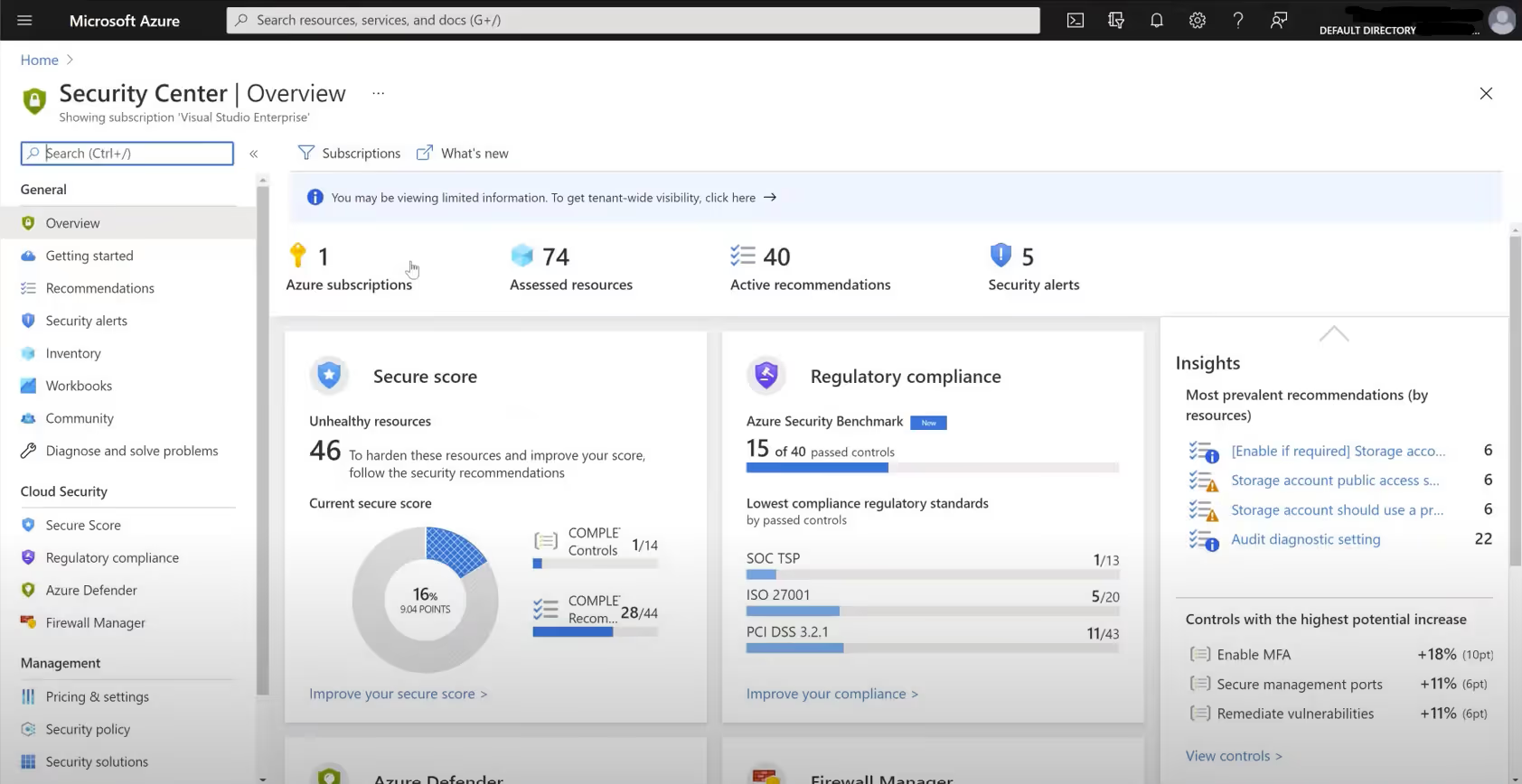
You will be able to view an assessment of your environment’s compliance against any regulatory requirements. It’s an ongoing assessment – there is something called freshness interval for everything. Some assessments are performed once every 24 hours, while the most critical ones are refreshed once every 30 minutes.
All the insights that you get through the Security Center have actionable, recommended steps. They can be manual or automated, but you’re receiving actionable insights and different reports on the security center recommendations.
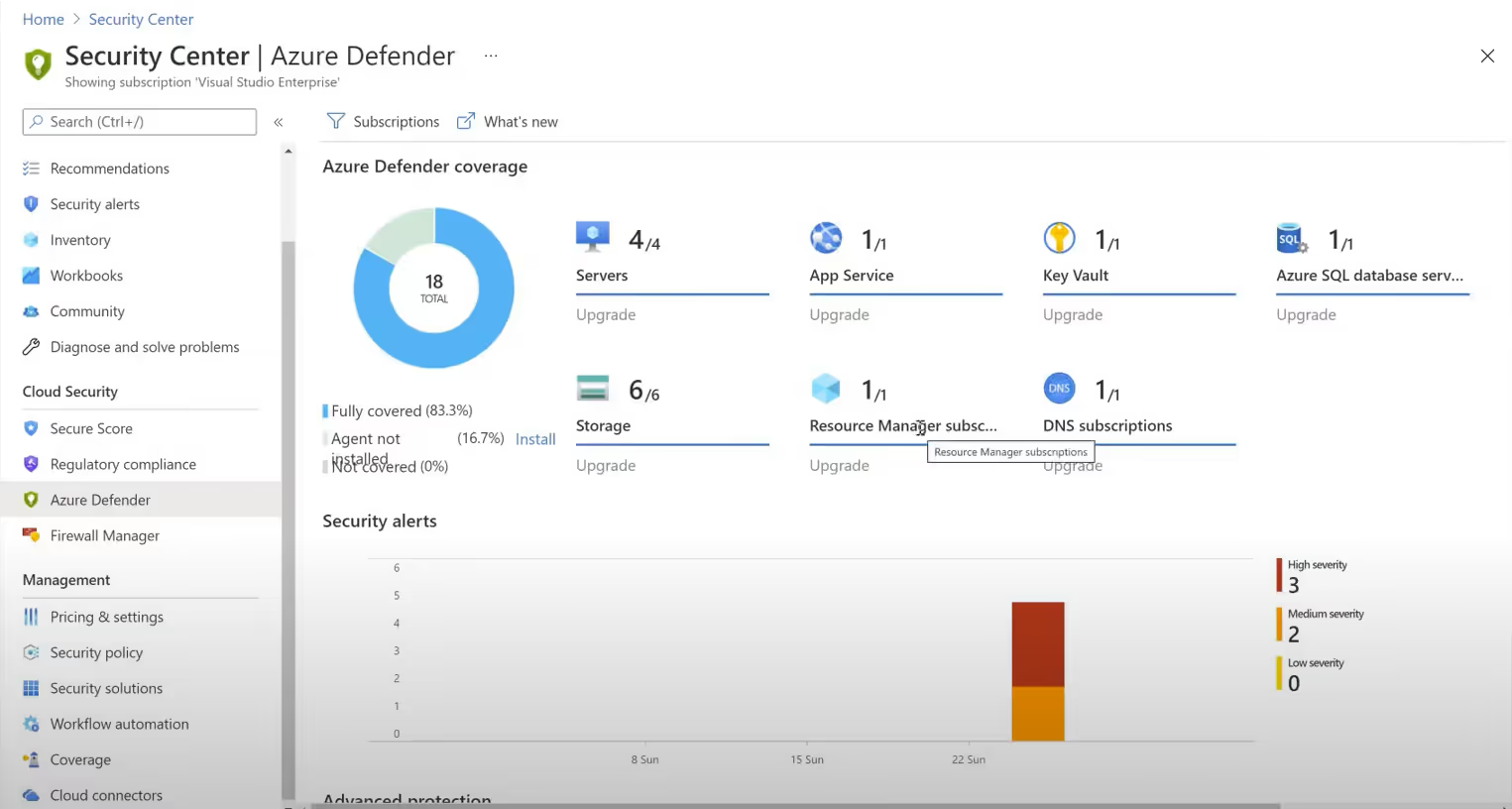
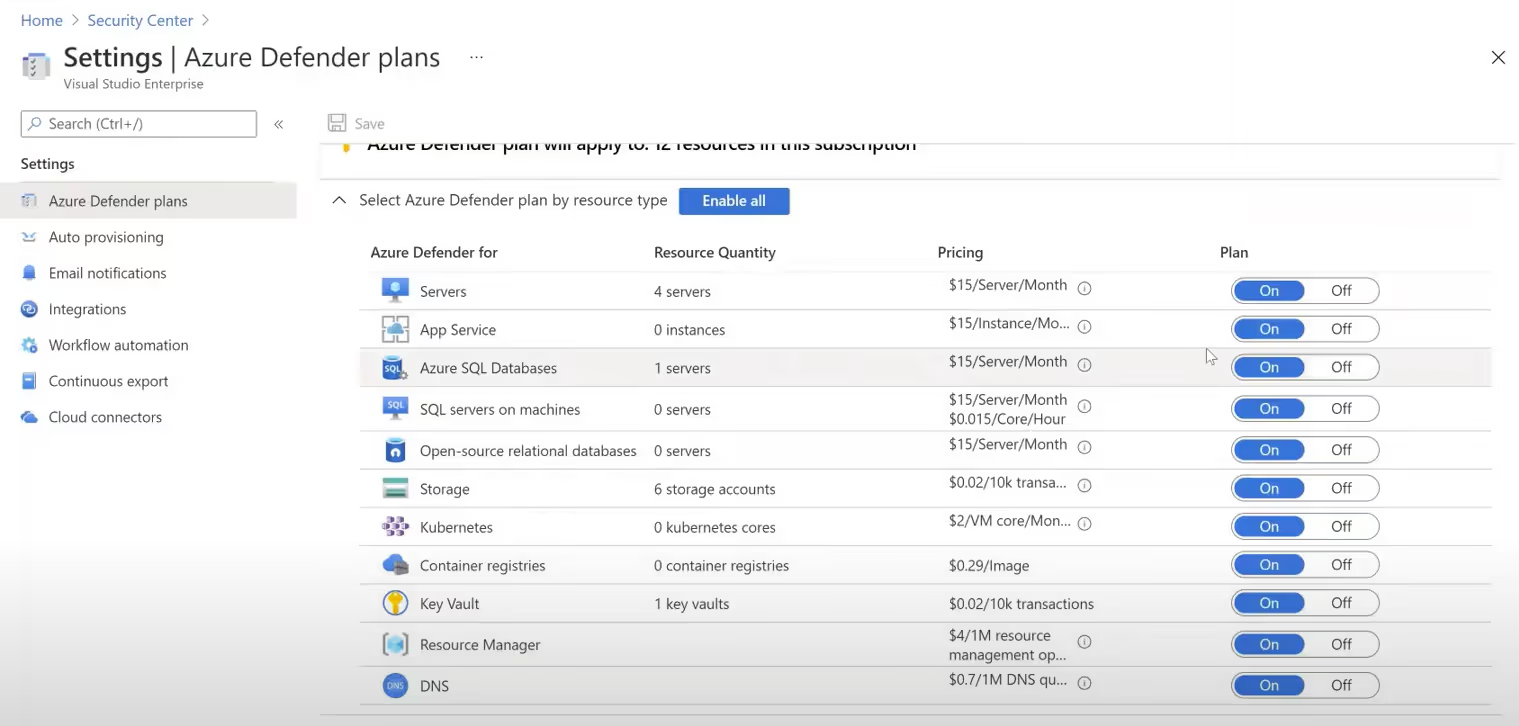
If you want to add more functionality, you can purchase Azure Defender. The upgrade will afford you a regulatory compliance dashboard with reports, adaptive application controls and networking hardening, and Just in Time VM access. This last feature enables approved users to open inbound management ports to their connection only (or IP range), for a limited time. The ports will automatically lock down after use. You’ll also receive threat protection for Azure VMs and non-Azure servers, as well as protection for supported PaaS services.
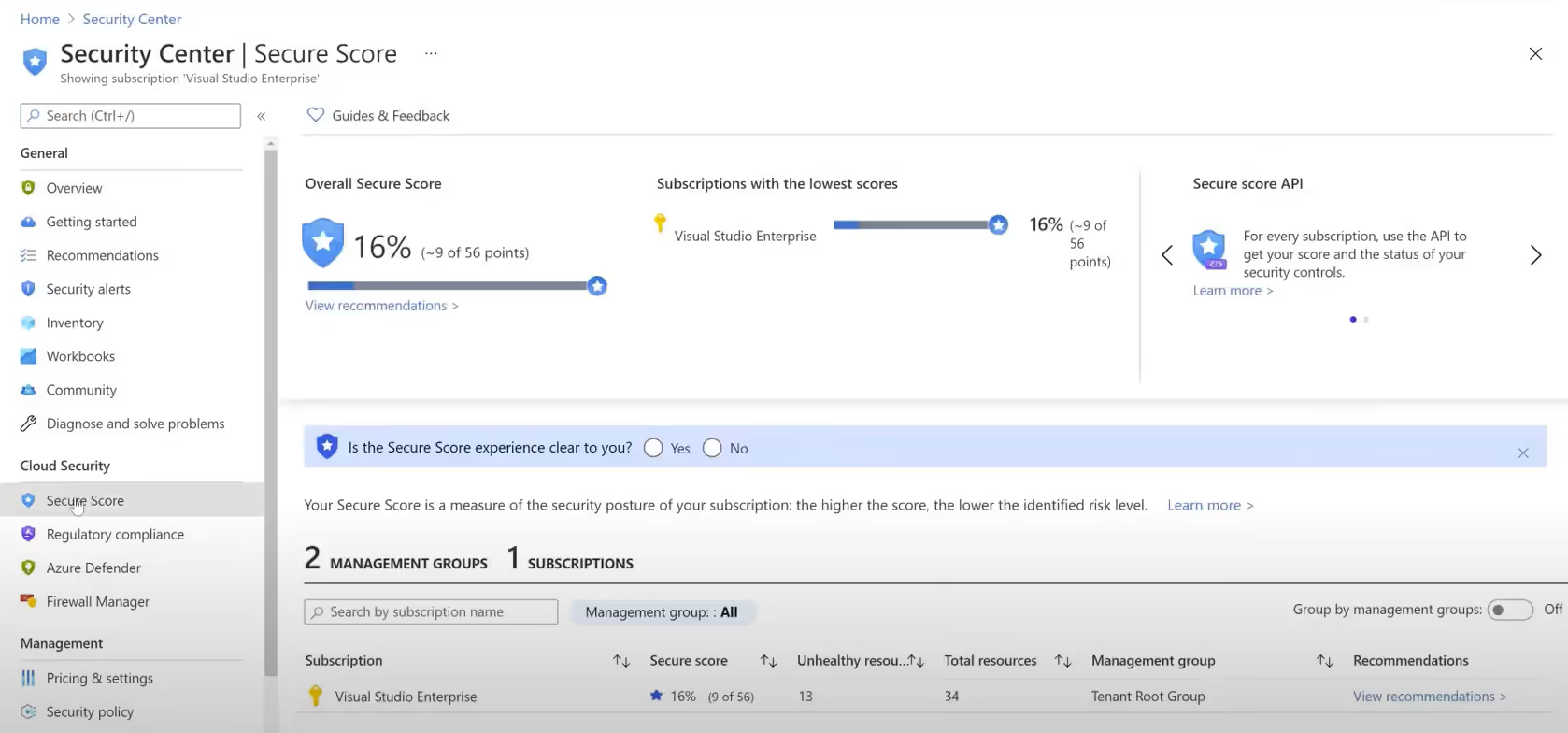
You can visualize the security state of your environment in a single glance by leveraging your Secure Score. Secure Score is the representation of your overall security posture boiled down to one number, offering a glimpse into your current posture and where you can improve. A higher score implies better security. It helps organizations report in a clear, concise manner the state of their security, provides visibility and control, and facilitates comparison with key performance indicators (KPIs). Your Security Score clearly illustrates opportunities for improvement and even allows you to compare your score with other similar organizations.
An Azure Policy definition is a parameter for a specific security condition that you want to control. It might look like assigning the use of tags on all resources, or controlling what type of resources can be deployed. These policy definitions can be adjusted to your custom requirements.
The policy definitions will need to be assigned (whether they’re built-in or custom). There are different types of policies you’ll encounter as well; for the most part you’ll encounter ‘Audit’ policies (ones that check specific conditions and ensure compliance), but you’ll also see ‘Enforce’ policies, which can be used to apply security settings.
When reviewing a recommendation, you may want to review the underlying policy – each recommendation will have one. This will help understand the system’s evaluation logic.
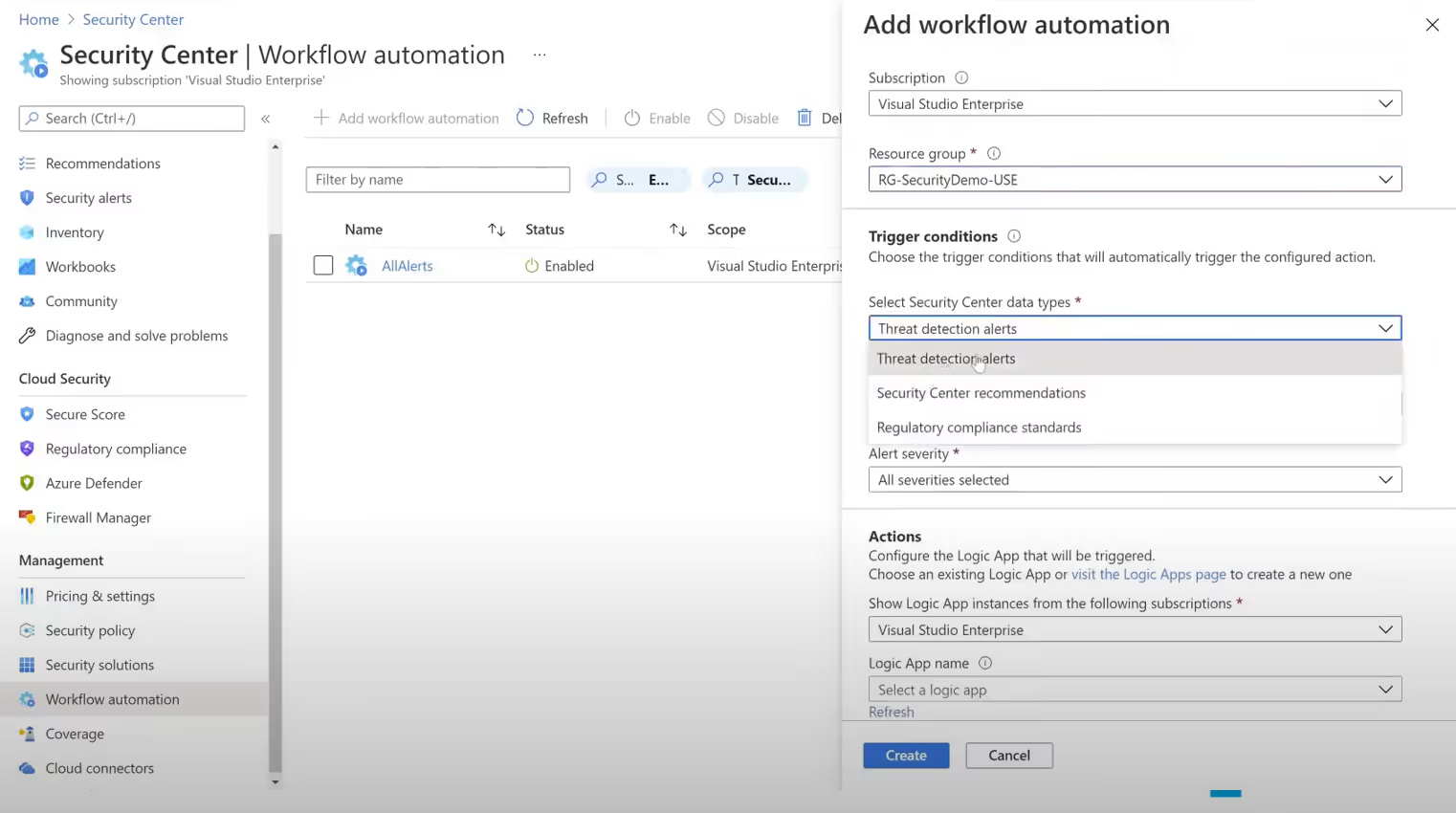
You can implement Logic Apps and triggers within your subscriptions and resource groups to perform automated security actions as well. These Workflow automations help maintain security even when you are not actively monitoring or remediating.
Recommendations are grouped into something called security controls. Security controls are a logical grouping of related security recommendations. If you want to enhance your Security Score, you must follow all the recommendations for a particular security control.
Each action for improvement is worth up to 10 points, and most are scored in a binary fashion. If you execute the recommended action, like turning on a recommended setting, you get 100% of the points. For other improvement actions, points may be given as a percentage of the total configuration.

Perhaps an improvement action states you get 10 points by protecting all your users with multi-factor authentication. You only have 50 / 100 total users protected, so you'd get a score of 5 points (50protected / 100 total x 10 max points = 5 points).
Each recommendation has a different impact on security score. Most recommendations will be policy driven – the Security Center will audit your whole environment and provide you with reports specifying which areas are not living up to policy expectations. Every recommendation has a different level of severity: high, medium, or low, depending upon its impact to the security of your infrastructure. It also features a freshness interval: anywhere from 30 min to 24 hours and sometimes in between that range.
When you receive recommendations, you’ll want to remediate them to make your environment more secure. You can either institute the changes manually or rely on automation.
If you’re addressing the issue manually, Azure will provide you with detailed documentation, links, and steps. If you want to automate the fixes, it’s even easier, just click the button and Azure will fix the issue behind the scenes.

Microsoft recognizes the diversity of cloud environments, so if you feel the suggested remediation is unnecessary in your case, you can opt-out. When you opt-out, you can either say you’ve mitigated this issue using a third-party solution or you are not leveraging the Microsoft solution for the issue. Security Center will ask you to affirm a waiver, essentially stating that you understand the risk of ignoring that recommendation, but you consent to taking the risk. Investing in the proper tools to enhance your security is essential for doing business in the modern era. Azure security center can help you strengthen your security posture by providing “at a glance” security updates via Secure Score, leveraging Azure policies behind the scenes, and keeping you compliant. In addition, Security Center recommendations can help you rapidly rectify any security concerns in your environment.
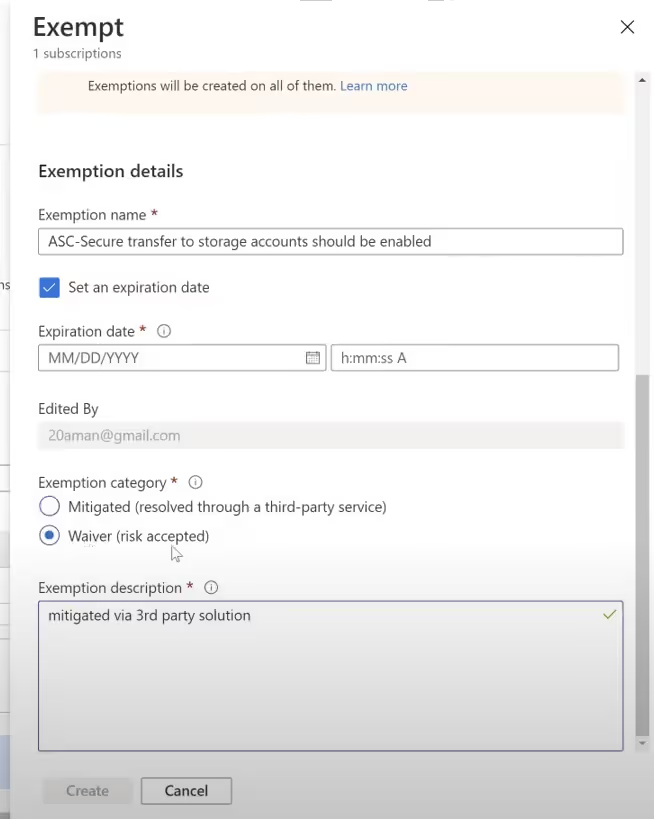
Every cloud environment is unique. Azure Security Center allows for flexibility in deployment by working across hybrid, on-premises, and multi-cloud architectures while also empowering you to customize your policy and even ignore or exempt yourself from specific recommendations. Together with Azure Defender and Azure Sentinel, Microsoft offers a powerful and constantly improving suite of information security management tools for today’s complex workloads.
