BLOG
Getting Started with Microsoft Azure Sentinel: Part 2
This is Part Two and the final entry in our introductory blog series on Azure Sentinel, Microsoft's new Security Information and Event Management (SIEM) tool for Azure environments. Read Part One here for information on what Sentinel is, how to set it up, and how to begin importing data from your Azure PaaS and IaaS.
In Part Two, we'll examine deeper functionalities within Sentinel including Machine Learning, queries, and automation.
Enabling Machine Learning in Azure Sentinel
There are three ways Machine Learning plays a role in Azure Sentinel:
- Built-in Machine Learning: you don't need to do anything here. It is already provided out-of-the-box. It provides advanced analytics and insights into any anomalous behavior by detecting any suspicious patterns.
- Building your own Machine Learning
- Fusion
Fusion tries to reduce alert fatigue. It is currently in public preview and uses state of the art scalable learning algorithms to correlate millions of lower fidelity anomalous activities into tens of high fidelity cases. You can enable ML (or Machine Learning) in Azure Sentinel by simply running the below command from an Azure Shell:
az resource update --ids /subscriptions/{Subscription Guid}/resourceGroups/{Log analytics resource Group Name}/providers/Microsoft.OperationalInsights/workspaces/{Log analytics workspace Name}/providers/Microsoft.SecurityInsights/settings/Fusion --api-version 2019-01-01-preview --set properties.IsEnabled=true --subscription "{Subscription Guid}"
Replace the following according to your environment:
- {Subscripiton Guid} - Subscription Id for your environment
- {Log analytics resource Group Name} - Resource Group Name for the Log Analytics workspace, which you connected to Azure Sentinel
- {Log analytics workspace Name} - Name of the Log Analytics workspace which you connected to Azure Sentinel
Once enabled, Fusion combines multiple yellow alerts, which themselves may not be actionable, into high fidelity security red cases. It looks at disparate products to produce actionable incidents so as to reduce the false positive rate. With this Microsoft ensures median 90% reduction in alert fatigue.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/connect-fusion
Running Queries in Azure Sentinel
Azure Sentinel uses the same query language as Azure Log Analytics. You can use this to perform an analysis of your security data. There are multiple sample queries readily available for you or you can write your own.
Below is an image of the Azure Sentinel Logs interface, where you will configure your queries. An explanation for each numbered area follows.
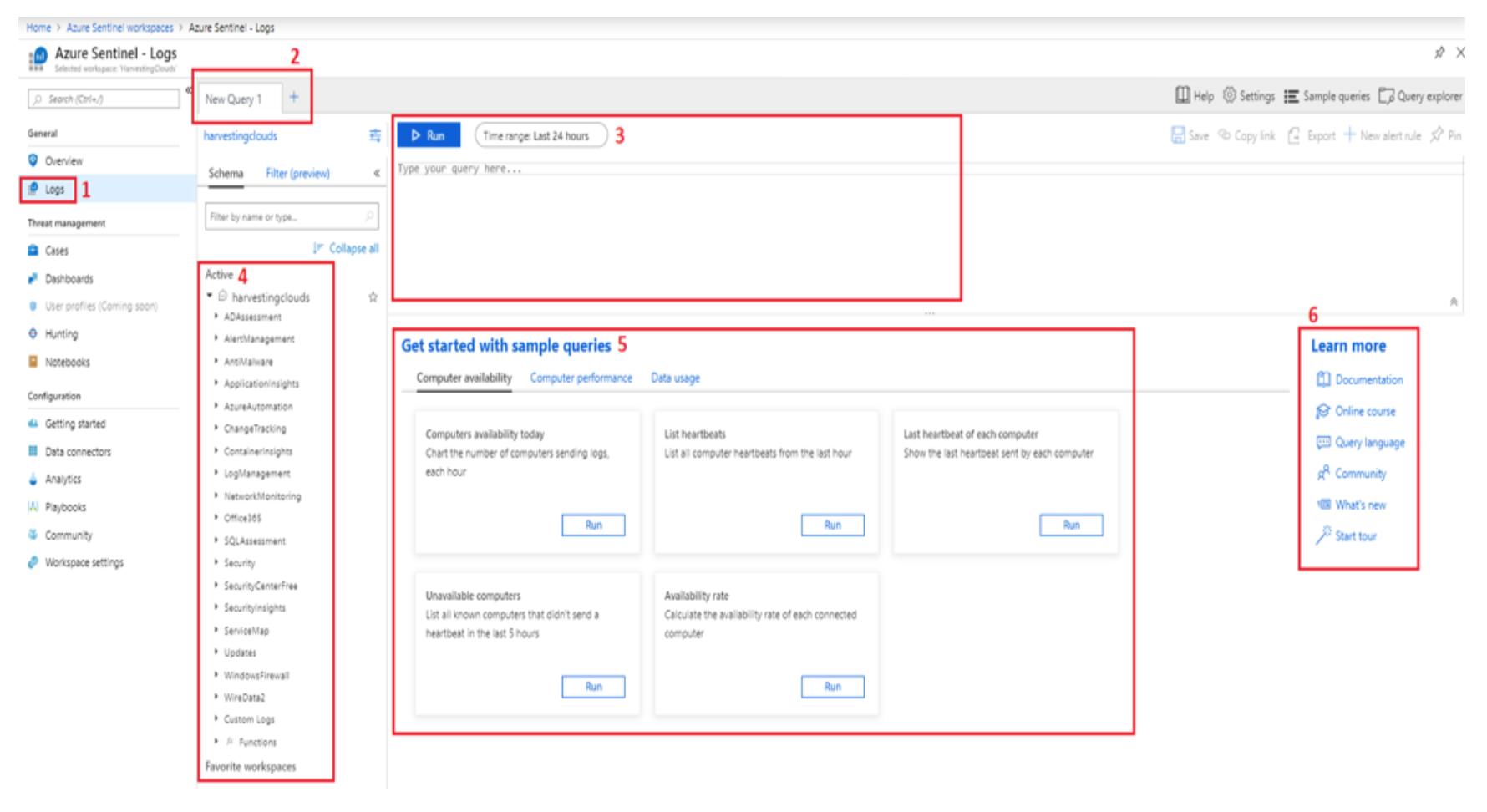
- You can access the queries by navigating to the Logs section.
- You can create multiple tabs, one for each query, to work on them separately and simultaneously.
- Next is the section where you actually write your query. You also filter the time range in this section. Once you have built your query you can click on the "Run" button to execute the query.
- You can inspect all the workspaces in your environment in this section on the left. You can also click on any source and can expand it to see various tables of data under it. You can even double click on these entries to auto add these to the query section.
- Multiple samples are provided to get you started.
- Finally on the right is the section for documentation, query language reference, and other useful information.
Try running the below sample query. Note that it requires the relevant connector to be already set up by you. Also note that there may not be data in your environment if you have just set it up, so you may want to give it some time before you can start seeing the data.
This query helps you inspect the Sign-Ins in your environment and look for any anomalies.
SigninLogs
| summarize count() by bin(TimeGenerated, 1h)
Automating Operations with Playbooks
You can build and run Playbooks in Azure Sentinel to automate security operations against various alerts. Playbooks are Azure Logic Apps workflows that you can easily author using in the portal designer.
You can author playbooks for various scenarios, such as:
- Blocking an IP address from where an attack may originate
- Locking a user account that may seem compromised
- Blocking an App Registration's access
- Resetting a User password
- Opening a Ticket in your ticketing system
- Blocking access to a Virtual Machine on a particular port
- Shutting down a Virtual Machine
- Sending an email notification
These can be triggered either manually or automatically when an alert is fired in Azure Sentinel. The integration is provided out-of-the-box in Azure. In a single playbook, you can have one or more actions taken together in an automated way.
Other Features
There are loads of other features in Azure Sentinel. In brief, these features are:
- Cases help you organize alerts and related entities and track these. A case can be generated by an alert in your system. You can then track and take actions on this case or assign it to someone in your team. A case will have status and severity attached to it to help you track it better.
- The Investigation Tool helps you understand the scope and root cause of a potential threat. You can drill into the related data for any event you want to investigate.
- Azure Notebooks are free hosted service to develop and run Jupyter notebooks in the cloud with no installation. It allows you to automate common investigative steps. You can also query Azure Sentinel data and compare with other services and build visualizations on that data to make it more meaningful.
- Hunting lets you reuse pre-built queries which are crafted by Microsoft security experts. This makes Azure Sentinel more proactive tool as compared to the reactive features we have seen so far. This helps you hunt for anomalies and security threats across your organization.
- Azure Sentinel on GitHub hosts various community provided resources, like sample Dashboards. Visit the official GitHub page at https://github.com/Azure/Azure-Sentinel.
Conclusion
Azure Sentinel is a key service from Microsoft that bridges a gap in security related to the cloud. It is the SIEM that provides a single pane of glass into the different aspects of security related to all of your environment, by not only bringing different Microsoft services together but also data from various third party providers as well. The Machine Learning and Automation capabilities make it the tool of choice for not just reactive but also proactive security measures for your whole environment.






















